Controversial T. Rex Soft Tissue Find Finally Explained | LiveScience
Controversial T. Rex Soft Tissue Find Finally Explained | LiveScience.

Controversial T. Rex Soft Tissue Find Finally Explained | LiveScience.

Army Scores a Super-Stealthy Drone That Looks Like a Bird | Danger Room | Wired.com.

China to launch moon rover on Monday: state media | AsiaOne.

Sentient code: An inside look at Stephen Wolfram's utterly new, insanely ambitious computational paradigm | VentureBeat | Dev | by John Koetsier.
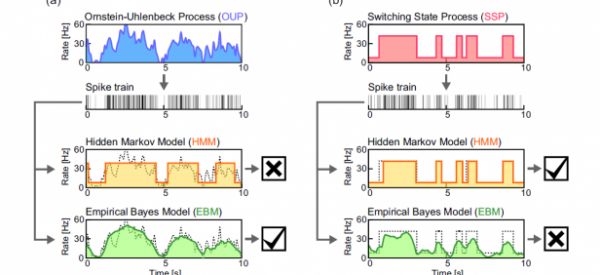
Solving the Neural Code Conundrum: Digital or Analog? | MIT Technology Review.

Dutch intelligence agency AIVD hacks internet forums – nrc.nl.
Physicists Find a Way to Study Coldest Objects in the Universe – Trending News – iTech Post.
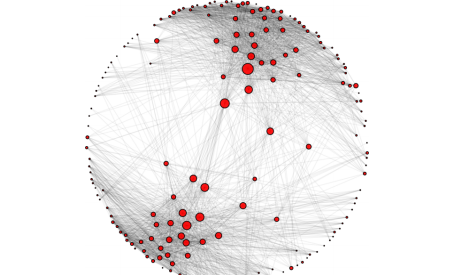
How to Burst the "Filter Bubble" that Protects Us from Opposing Views | MIT Technology Review.
Facebook App requires users agree to be monitored by microphone at any time without their permission | RedFlagNews.com.