
Innovators: Building an electric car for speed | Marketplace.org
Innovators: Building an electric car for speed | Marketplace.org.

Innovators: Building an electric car for speed | Marketplace.org.
'Silent but deadly' Java security update breaks legacy apps – dev • The Register.
Analysis: Inventory mountain adds to pain for Chinese solar firms | Reuters.

Launch Party: a crowdfunding revolution ignites the next space race | The Verge.
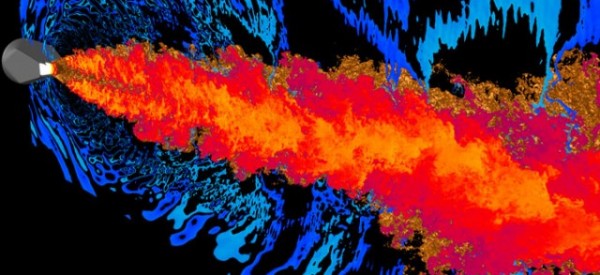
How to use a million-core supercomputer—without it blowing up in your face | Ars Technica.

Wind Beats Out Natural Gas To Become Top Source Of New Electricity Capacity For 2012 | ThinkProgress.

Building a lunar base with 3D printing / Technology / Our Activities / ESA.
Security experts on Java: Fixing zero-day exploit could take 'two years' | ZDNet.
Apple blocks Java on Macs due to vulnerabilities – Technology on NBCNews.com.
Disable This Buggy Feature On Your Router Now To Avoid A Serious Set Of Security Vulnerabilities – Forbes.